INTRODUCTION
The advancements in the personal computers (PCs) (mainly in the hardware including the size and weight of the computers along with the high speed and performance with the lower cost) and communications (including the internet call and wireless, WANs, and the calling software) had introduced the idea of the cellular phones. It implies clients don’t need to be fastened on costly wired workstations to share information. They only need to have mobile PCs that is a portable computers and will use to share information by using wireless networks. In the 21st century, Mobile PC will be the correspondence vehicle for individuals: the opportunity to share information anytime anywhere around the globe without going. Mobile computing is firmly relying upon the accessible foundation of disseminated frameworks. Accordingly, it can consider augmentation of circulated frameworks computing. Moreover, the expansion of thoughts like mobile operators forces portability to an extensive variety of innovative methodologies for future disseminated data frameworks (Ahmed & Hossain, 2014).
The advantages of on-the-move network connectivity are self-evident. In any case, there are numerous genuine systems administration and framework problems to be unraveled before the full advantages of mobile computing systems are practically acknowledged. Among all these; one basic issue is security. The study undertaken intends to review the existing literature to highlight the critical issues relating to mobile computing. Lastly, the study will discuss the security problems emerging from modern, innovative ways to deal with mobile computing.
Analysis of Mobile Viruses
Malicious agents those particular target cell phones and handheld gadgets are on the ascent. The most particular forms of these were viewed as safe since these were not composed to spread starting with one gadget and then onto the next. The latest versatile infections, be that as it may, are fit for spreading to close-by devices using Bluetooth, and, in this manner, represent a more genuine danger to big business systems. In what tails, we list the most popular spreading instruments, target stages, and customer vulnerabilities of versatile infections found to date. Additionally, points of interest on them are accessible on various security-merchant sites. • One of the most punctual infections composed for handheld gadgets (Palm PDAs), is the PalmOS Liberty. An infection must be physically introduced and executed for it to wind up noticeably dynamic. The infection erased all applications and databases on a Palm OS-good gadget. The Liberty infection and other comparable Trojans by their plan are not prone to spread rapidly because of their manual contamination process and in this manner, speak to moderately low risk. • An infection for Palm OS, called Phage was imagined for the most part as a show — it could spread starting with one PDA and then onto the next if contaminated documents were shared using infrared radiating or a docking station. It was a change from the manual Infection.
According to Dinh, Lee, Niyato, & Wang, (2013) is the main known malware to assault MultiMedia Cards (MMC) streak memory of cell phones — it is a trojanized rendition of Symbian application InstantSis that enables clients to repack as of now introduced SIS documents and duplicate them to another telephone. Be that as it may, when clients attempt the romanized version, a payload hinders the memory card by setting an arbitrary password to it and erases basic framework and mail catalogs.
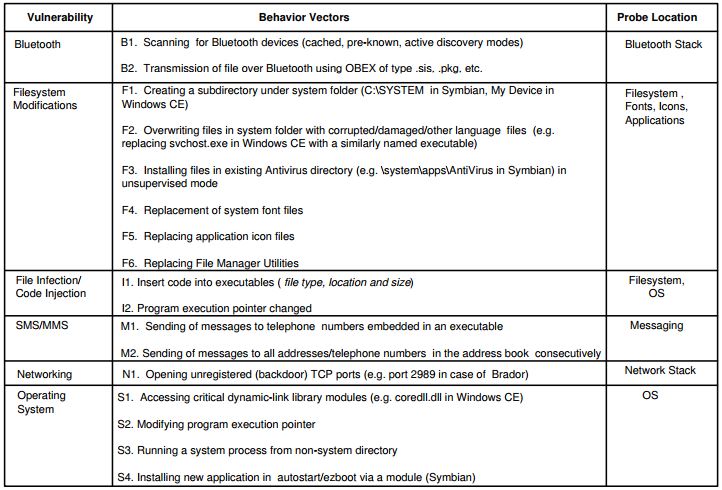
Figure 4.1: Common behavior vectors of existing mobile viruses
Model of a Generic Mobile Virus with a specific end goal to consider spread models and control systems of portable infections, the author has fused versatile malware proliferation into our fine-grained agent-based malware modeling (AMM) structure depicted prior (Chandrasekar & Jayaprakasan, 2014). It unequivocally models each wandering handset in a portable system utilizing an arrangement of administrations, for example, email, SMS/MMS, Bluetooth, and so on. As clarified in the introduction, a specialist-based demonstrating approach with regards to handset infection/worm proliferation unwinds the homogeneity and flawless blending presumptions of standard epidemiological models by (i) joining heterogeneity in operator properties (e.g., distinctive portable OS’s, handsets), (ii) displaying the state moves of an operator as an unequivocal stochastic process, and (iii) permitting very organized topologies of administration associations (e.g., SMS senders and collectors) among the operators. The administration cooperation topologies can be produced from movement follows examined from a true system and contribution to the specialist-based model as we have accomplished for SMS.
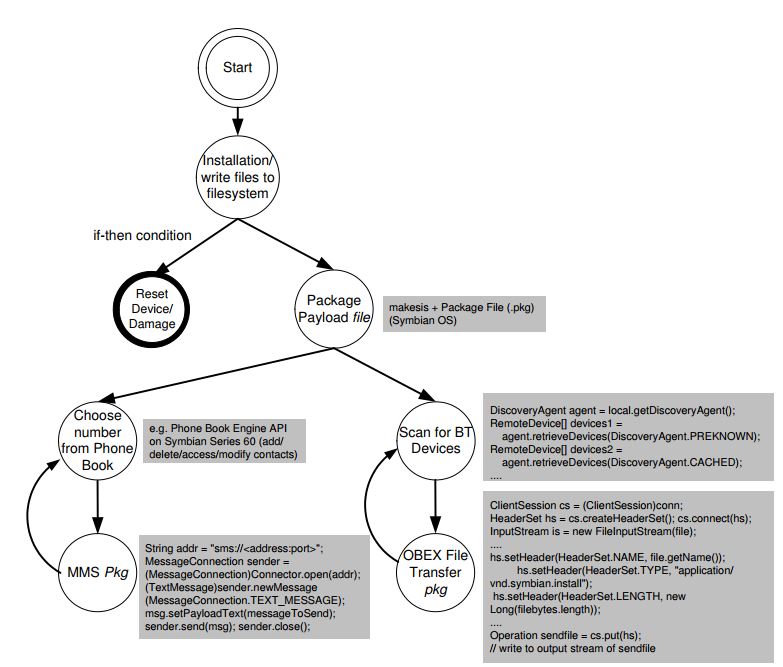
Figure 4.2: State diagram of a mobile virus in AMM
Crossover Malware
Before we discuss potential vulnerabilities of Bluetooth and SMS/MMS services that can be exploited for malicious purposes, we must mention an emerging class of malware called “crossover” infectors that can spread from mobile devices to desktop PCs, or vice versa. For example, Rizzo, (2016) is a Symbian SIS file trojan that disables a number of applications on Nokia series 60 cell phones in addition to installing variants of skulls and Cabir. However, the most significant characteristic of Cardtrap is that it also installs three Windows worms (Win32.Rays, Win32.Padobot.Z, and Win32.Cydog.B) onto the device’s memory card. Once the card is inserted into the PC, Padobot.Z will attempt to start automatically on machines running Windows OS via the “autorun.Ini” file.
However, since Windows does not support autorun from a memory card, the current version depends on user interaction to be launched. Conversely, a recent virus called Crossover spreads from Windows desktop PCs to mobile devices running on Windows Mobile Pocket PC. Once it is installed on a Windows PC, the virus makes a copy of itself and adds a registry entry pointing to the new file so that the payload is activated each time the machine is rebooted (Padgette, 2017). It then waits for an application (e.g., ActiveSync) for synchronizing Pocket PC devices with the infected Windows desktop PC. When a connection is detected, it copies itself over to the Pocket PC device, deletes all files in the My Documents directory, copies itself to the system directory, and places a link to itself in the startup directory. Current-generation crossover viruses such as Cardtrap and Crossover are not powerful enough to cause concern at present. Nonetheless, these viruses give rise to the future possibility of an attacker using Bluetooth or SMS/MMS-capable handset to transfer a malicious agent designed to spread to millions of desktop PCs on the Internet (Padgette, 2017).
Bluetooth Exploits for Mobile Malware
There are brute-force techniques such as RedFang that can be used to guess the Bluetooth device identifier (48-bit) of a remote device. The last three bytes of the identifier should be unique to each Bluetooth device. In practice, some cellular phone manufacturers choose not to assign a unique Bluetooth identifier to each phone. By reducing the size of the searchable address space (e.g., when the manufacturer of the remote device is known, i.e., the device is within the visual range) and by improving the address search algorithm, it is now possible to find all hidden Bluetooth devices within the range in about four and half days (Hassan, Bibon, Hossain, & Atiquzzaman, 2017). It means that the spreading rate of a mobile virus based on current-generation brute-force proximity scanning techniques is relatively low. However, further reduction in time is possible due to pseudo-random number generators used for addresses by device manufacturers, and by employing an approach similar to permutation scanning used by regular Internet worms. The brute-force approach is not a limiting factor for a malicious attacker who uses a Bluetooth-enabled device simply to launch a crossover worm or virus (Hassan et al., 2017).
More Read: Gaming Assets Service
AMM for SMS and Bluetooth Threats
MS address spoofing is an emerging threat that allows a malicious agent to make an SMS message appear as though it came from a different user and network. This is similar to how email spams and spam relays work. The SMS web-based gateways can also be exploited to spoof the message’s origin. There appears to be even an open-source tool on the Internet called “SMS Spoof” for Palm OS that allows any user to send spoofed messages through any SMSC supporting the EMI/UCP protocol (Milosevic, Regazzoni, & Malek, 2017).
Conclusion
The expansion of cell phones, for example, advanced cells, PDAs, and handsets have presented new versatile infections, for example, Commwarrior, Mabir, and so on., that can spread through SMS/MMS messages and by missing Bluetooth vulnerabilities. In this study, the author has investigated the current versatile infections t range in about four and half days. This means that the spreading rate of a mobile virus base extricates an arrangement of their basic conduct vectors that can be utilized to create portable infection identification and control calculations. The author has examined the vulnerabilities of Bluetooth and SMS/MMS informing frameworks top to bottom and called attention to the vulnerabilities that might be misused by future portable infections.
The author has likewise built up the state outline of a non-exclusive versatile infection that can spread through SMS/MMS and Bluetooth. The revelation, disease, and replication conditions of the nonspecific infection were actualized in the AMM demonstrating structure, to examine its engendering. The author utilized information from an expansive certifiable cell bearer to produce a downsized topology of an SMS arrangement and considered the proliferation of the portable infection. The outcomes demonstrate that because of the heterogeneity of portable handset stages and without scale nature of the SMS organize, the development rate of a versatile infection missing SMS messages is little. Be that as it may, the development rate increments fundamentally when these handsets are very defenseless against Bluetooth abuses.
There are various zones where future work can be sought after. The behavioral discovery approach introduced in this paper ought to be incorporated with an ongoing regulation system that can specifically control distinctive administrations accessible on the handset. This will guarantee that voice, and different administrations (e.g., route, nearby inquiry, and so forth.) on the handset are independently observed by the regulation layer, e.g., voice calls ought not to be affected by malware that objective just Bluetooth or SMS/MMS informing. It will likewise be important to create effective over-the-air or Internet-based methodologies for transferring new conduct marks for the identification subsystem.
The results of the study indicate that due to the heterogeneity of mobile handset platforms and the scale-free nature of the SMS network, the growth rate of a mobile virus exploiting SMS messages is small. But the growth rate increases significantly when these handsets are highly vulnerable to Bluetooth exploits. There are several areas of future work such as improving our simulator so that larger topologies in the order of millions of handsets can be simulated, and investigating of novel mobile virus detection and containment algorithms.
References
Ahmed, M., & Hossain, M. A. (2014). Cloud computing and security issues in the cloud. International Journal of Network Security & Its Applications, 6(1), 25.
Chandrasekar, S., & Jayaprakasan, V. (2014). Automatic Detection and Restraining Mobile Virus Propagation using Android.
Dinh, H. T., Lee, C., Niyato, D., & Wang, P. (2013). A survey of mobile cloud computing: architecture, applications, and approaches. Wireless Communications and Mobile Computing, 13(18), 1587–1611.
Hassan, S. S., Bibon, S. D., Hossain, M. S., & Atiquzzaman, M. (2017). Security threats in Bluetooth technology. Computers & Security.
Milosevic, J., Regazzoni, F., & Malek, M. (2017). Malware Threats and Solutions for Trustworthy Mobile Systems Design. In Hardware Security and Trust (pp. 149–167). Springer.
Padgette, J. (2017). Guide to bluetooth security. NIST Special Publication, 800, 121.
Rizzo, L. K. (2016). Threats and benefits of data-hiding methods used in smart mobile devices. Utica College.