Spear phishing is an email or electronic communications scam which aims to target an organization or a specific individual to steal their private data for the wrong purposes often. The cybercriminals achieve their targets by installing the malware on the target machines through the internet; they often deceive the targets by looking like a trustworthy source and transmitting a bogus code to the computers. The double attack email to deceive people by sharing their perceptive information; These types of attacks lead to huge losses of important data and sensitive information. The phishing attack easily misleads the security measures of an organization through double attack email. There are three major phases of phishing: fake phishing emails, setting up fake websites, and fabricating stolen information (Sharma, 2014).
Many attackers and cybercriminals in these attacks are sponsored by the government and have an objective to resell the information obtained illegally or stolen from the target computers. It is difficult to detect phishing emails and save sensitive information from falling into the wrong hands. The employers of today need awareness of these threats with education and technology, which is creating an adverse effect on the government and private organizations’ data. Various classification of spear phishing attacks includes lure and exploit payload. However, to make the data safe, there are various security systems such as threat model, impersonation model, etc. (Ho et al., 2014).
Problem Statement
Spear phishing is one of the social engineering attacks that cause dangerous effects on a company’s sensitive data. Organizations’ data is much more important to them, and securing that data is their core responsibility. The analysis of credentials of spear phishing is important for enterprise settings to alert the security models to avoid huge data loss. However, organizations need a model that could effectively prevent the attack (Ho et al., 2014).
Thesis Questions
1. What are the approaches to detect credential spear phishing attacks?
2. What is the taxonomy for spear phishing attacks?
3. Which security system could address a safer mode to the company’s data?
4. What are the features and technology in the proposed security system?
Significance and methods for the Research:
This thesis will introduce a novel system that can identify phishing emails using its algorithm. The proposed system would be able to identify phishing emails using a big data intelligence mechanism. The system will identify phishing emails using the patterns and behaviors. The proposed system will work as a filter for all the emails of an organization. A specially crafted algorithm will use to identify phishing emails through their behavior. The further front end of the system will be implemented to control the email flow by a system administrator. The administrator can blacklist or whitelist special domains if the system identifies false positive incidents. The goal of this research is to develop a platform that can efficiently identify phishing emails. (Frank, 2017)
More Read: Visual effects courses in Mumbai
The thesis will rely on qualitative, which will be done through the collection of literature reviews from past authentic research papers. However, the research strategy, philosophy, and approach will be analyzed through research onion by Saunders.
The LBNL’s detection data is presented in the following table, which contains the real-time detection results for phishing emails from Sept 1, 2013, to June 14, 2017.
Alert Classification Name spoofer Previously unseen attacker Lateral attacker Total Count
Spearfish: known 2 2 2 6/7
+ successful attack
Spearphish: 1 1 0 2/2
unknown
+ successful attack
Spearphish: failed attack 3 6 0 9/10
Total Spearphish Detected 6 9 2 17/19
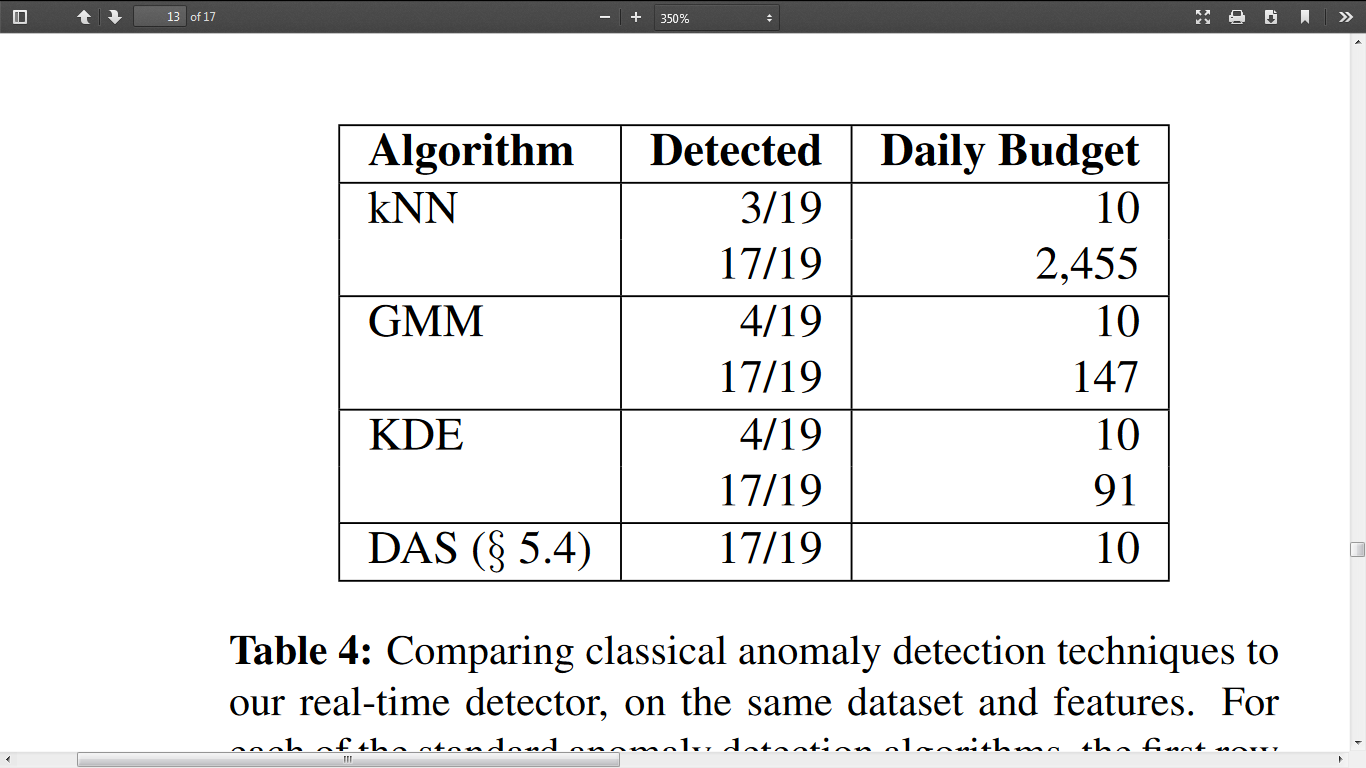
The limitation of LBNL NDS was that Dropbox allowed users to host static HTML pages which were not visible to the organization, which is a limitation of the detector. The following table shows the results of the detection by using the algorithm. (Ho, 2014)
References
Groom, Frank M, Kevin M Groom, and Stephan Jones. Network And Data Security For Non-Engineers. Boca Raton: CRC Press, Taylor & Francis Group, an Informa Business, 2017. Print.
Jakobsson, Markus, and Steven Myers. Phishing And Countermeasures. Hoboken, N.J: Wiley-Interscience, 2007. Print.
“Phishing Security Test | Knowbe4.” Knowbe4.com. N.p., 2017. Web. 21 Oct. 2017.
Sharma, Ashish, and Grant Ho. Detecting Credential Spearphising Attacks In Enterprise Settings. 1st ed. 2014. Print.
Sood, Aditya K, and Richard J Enbody. Targeted Cyber Attacks. Waltham, MA: Syngress, 2014. Print.