Introduction
Data prevention is essential to all companies because any data leakage can damage a company’s reputation which can result to lose. With the rise of theft of vital data, companies have found the best way to protect their data, and therefore, several companies are turning to DLP as the best alternative to safeguard information. According to Baylor (2017), data loss protection ensures that confidential information does not leave an organization and prevent authorized access to confidential data. The implementation of DLP requires a culture change since it introduces a new way of handling data and other sensitive information o the company. Prior to implementation of data loss prevention (DLP) proper analysis of data which includes backing up sensitive information must be conducted.
Data Loss Prevention (DLP) implementation strategy
The best strategy for the implementation of DLP is to develop a clear plan which layout clear procedure which would be adhered to make sure the implementation of DLP is successful. First, the sensitive data must be identified by the project team. This is done to prevent the loss of any data during the implementation stages. At this stage, the organization must make sure that all data on transit, stored and in house are properly protected through protection of the channel. The second step is defining policy which shall be used to guide the data. Once the sensitive data has been identified an organization must derive a policy to protect the identified information from getting lost or leaked to the third party. The policy must involve some rules which can protect sensitive information such as no leaking or talking of credit card information.
The third stage of implementation strategy is to determine the flow of information. This is done to make sure the source and the flow of data is understood so that the project team understand where exactly the software would be implemented. It is conducted to make sure that a close monitoring or information governor are put in place (Baylor, 2017). In most cases, this is conducted through questionnaires. The fourth step is to identify the business owners. This is an essential stage since the company uses internal mechanism to identify owners of the data. It makes sure that the leak is sealed and mixture of data is avoided. It should be done to highlights the contact person in any case sensitive data is lost. The final stage is the deployment of Data loss prevention software to safeguard the company.
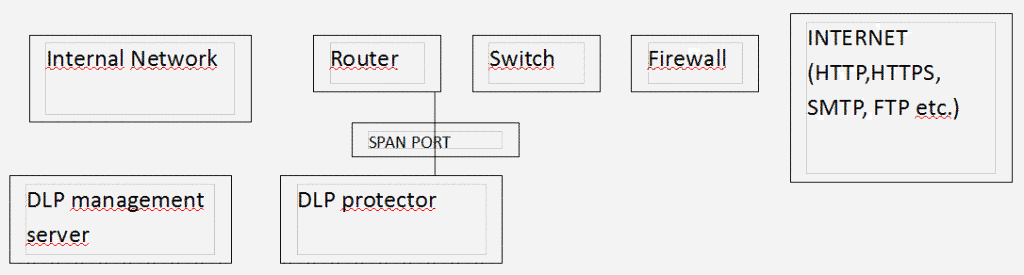
Figure 1: Data Loss Prevention Deployment diagram
Data Loss Prevention Software
There are varieties of DLP software which can be used to protect organization’s sensitive data. Some of the software is Comodo Dome protection, Spirion McAfee, Symantec Data Loss Prevention, Trustwave, check Point and Digital Guide Data Loss Protection. Each of these softwares has specific unique features which make the different and used for specific areas (Fearn, 2017). All data loss prevention software protects unauthorized access to the system, leakage of sensitive information. Some are installed on the cloud system to protect cybercrime and any other data breaches which can be attempted.
Symantec Data Loss Prevention
It is unique software used to monitor and protect sensitive data as well. Symantec Data Loss Prevention is scalable, it has impressived cloud coverage, and too enterprise oriented software. It is desktop oriented software with capabilities to manage, monitor and track data. It is also one of the best DLP software for cyber security since it offers protection coverage for both consumers and businesses. It has the ability to store and monitor information whereby it provides platform to system administrator to monitor data performance and hence track any unauthorized entry in real time.
Mimecast Data Loss Prevention
This is DLP software which is used to prevent data from malicious or accidentally leaked information. The software is installed in the port to monitor any activities which might be suspicious. It prevents data loss from the organization by stopping the email leak to make sure that all information leaving the system is not confidential.
Comodo Dome
The Comodo Dome is also one of the DLP software which is used in the protection of data. It is used mostly in cloud computer to monitor and gain mobility. It is used to scan and monitor emails and transfer all outbound emails and traffic so that any unauthorized entry could be detected before causing any damage. It is therefore, important to note that the only different which exist among the DLP softwares are the features and some perform specific role. The software is best suited for cloud computing system since it blocks ports which can be used by a third party to access the system.
Drawbacks
The implementation of DLP may create a lax in the prevention of data and therefore, makes the system more insecure. The fact that DLP is not a technology compromise the entire system and a contracted company to safeguard an organization system can as well access similar data. The DLP is a very expensive project to implement and maintaining is also expensive therefore, this can discourage other companies to implement it. The financial support requires in terms of implementation and maintenance might be a lot for some companies. It is a business product not a technology and therefore, it does not offer any technological solution to the problem. It can block business process of a company instead of processing business and this might impact negatively on a company performance.
References
Baylor, K. (2017). 12 Steps to DLP Best Practices. https://www.nsslabs.com/linkservid/13C2364A-5056-9046-931EC4F06A25968B/ , 2-34.
Fearn, N. (2017). Best data loss prevention software in 2017. Avoid Data Breach , 2-15.